You may find it useful to study specific samples of Computer Resume for IT jobs athttp://www.bestsampleresume.com/computer-resumes.html
5. Study the CV of Paul W Cair (Appendix 2). Then write your own CV in the same way. For the purpose of this task, you can invent experience and assume you have passed all your examinations. UNIT 5. INFORMATION SECURITY
READING ACTIVITIES
1. Read the text and find the answers to the following questions. 1. What does data encryption provide? a. privacy b. integrity с. authentication. 2. A message encrypted with the recipient's public key can only be decrypted with a. the sender's private key b. the sender's public key с. the recipient's private key. 3. What system is commonly used for encryption? 4. What is the opposite of 'encrypt'? 5. A message-digest function is used to a. authenticate a user b. create a MAC с. encrypt a message. 6. What information does a digital certificate give to a client?
SAFE DATA TRANSFER
Secure transactions across the Internet have three goals. First, the two parties engaging in a transaction (say, an email or a business purchase) don't want a third party to be able to read their transmission. Some form of data encryption is necessary to prevent this. Second, the receiver of the message should be able to detect whether someone has tampered with it in transit. This calls for a message-integrity scheme. Finally, both parties must know that they're communicating with each other, not an impostor. This is done with user authentication. Today's data encryption methods rely on a technique called public-key cryptography. Everyone using a public key system has a public key and a private key. Messages are encrypted and decrypted with these keys. A message encrypted with your public key can only be decrypted by a system that knows your private key. For the system to work, two parties engaging in a secure transaction must know each other's public keys. Private keys, however, are closely guarded secrets known only to their owners. When I want to send you an encrypted message, I use your public key to turn my message into gibberish. I know that only you can turn the gibberish back into the original message because only you know your private key. Public- key cryptography also works in reverse - that is, only your public key can decipher your private key's encryption. To make a message tamper-proof (providing message integrity), the sender runs each message through a message-digest function. This function within an application produces a number called a message-authentication code (MAC). The system works because it's almost impossible for an altered message to have the same MAC as another message. Also, you can't take a MAC and turn it back into the original message. The software being used for a given exchange produces a MAC for a message before it's encrypted. Next, it encrypts the MAC with the sender's private key. It then encrypts both the message and the encrypted MAC with the recipient's public key and sends the message. When the recipient gets the message and so decrypts it, they also get an encrypted MAC. The software takes the message and runs it through the same message-digest function that the sender used and creates its own MAC. Then it decrypts the sender's MAC. If the two are the same, then the message hasn't been tampered with. The dynamics of the Web dictate that a user-authentication system must exist. This can be done using digital certificates. A server authenticates itself to a client by sending an unencrypted ASCII-based digital certificate. A digital certificate contains information about the company operating the server, including the server's public key. The digital certificate is 'signed' by a trusted digital-certificate issuer, which means that the issuer has investigated the company operating the server and believes it to be legitimate. If the client trusts the issuer, then it can trust the server. The issuer 'signs' the certificate by generating a MAC for it, then encrypts the MAC with the issuer's private key. If the client trusts the issuer, then it already knows the issuer's public key. The dynamics and standards of secure transactions will change, but the three basic tenets of secure transactions will remain the same. If you understand the basics, then you're already three steps ahead of everyone else.
2. Match the functions 1-4 with the keys A-D.
3. Match the terms 1-6 with the statements A-F.
4. Mark the following statements as True or False. Correct the false ones. 1. A message encrypted with a public key can be decrypted by anyone. 2. To send a secure message you must know the recipient's public key. 3. Secure messages are normally encrypted using a private key before they are sent. 4. A message can be reconstructed from its MAC. 5. Two messages can often have the same MAC. 6. A digital certificate is sent to a client in an encrypted form. 7. A digital certificate should be signed by a trusted digital-certificate issuer. 8. A MAC is used to check that a message has not been tampered with. 5. Put the following sentences, about sending a secure email, in the correct order.
A. The message is decrypted with the recipient's private key. B. The message is received by the recipient. C. The message is encrypted with the recipient's public key. D. The message is sent by the sender.
6. Read the text and find the answers to the following questions.
1. Name 3 areas of computing that companies rely on more and more. 2. What can intimidate even the most experienced network manager? 3. What 3 types of peripheral storage devices do most companies rely on for backing up data and storing information? 4. What type of data-intensive application do companies rely more heavily on? 5. What has kept the SCSI bus from evolving rapidly? 6. What traditional LAN interface is mentioned in the text? 7. Name 2 drawbacks of NAS. 8. What type of server can be connected to a SAN? 9. In what 2 ways will a SAN lighten your server's workload? 10. What types of cabling can be used with Fibre Channel?
DOING THE SAN THING
As companies rely more and more on e-commerce, online-transaction processing and databases, the amount of information that needs to be managed and stored on a network can intimidate even the most experienced of network managers. While servers do a good job of storing data, their capacity is limited and they can become a bottleneck if too many users try to access the same information. Instead, most companies rely on peripheral storage devices, such as tape libraries, RAID disks and even optical storage systems. These devices are effective for backing up data online and storing large amounts of information. But as server farms increase in size and companies rely more heavily on data intensive applications, such as multimedia, the traditional storage model isn't quite as useful. This is because access to these peripheral devices can be slow, and it might not always be possible for every user to easily and transparently access each storage device. The most basic way of expanding storage capacity on the network is to hang disk arrays or other storage devices off servers, using the SCSI interface or bus. While SCSI has been a workhorse over the years for connecting peripherals at a relatively fast speed, distance limitations have kept this particular bus interface from evolving rapidly. The SCSI standards put a bus length limit of about 6m on devices. While this distance limitation doesn't really affect connecting storage devices directly to a server, it does severely restrict placing RAID and tape libraries at other points on the network. This is where the concept of Network Attached Storage (NAS) comes in. NAS is simple in concept and execution: disk arrays and other storage devices connect to the network through a traditional LAN interface, such as Ethernet. Storage devices would thus attach to network hubs, much the same as servers and other network devices. However, NAS does have a few drawbacks. First, network bandwidth places throughput limitations on the storage devices. Another downside to NAS is the lack of cohesion among storage devices. While disk arrays and tape drives are on the LAN, managing the devices can prove challenging, since they are separate entities and not logically tied together. NAS has its place as viable storage architecture, but large companies need something more. Large enterprises that want the ability to store and manage large amounts of information in a high-performance environment now have another option: the Storage Area Network (SAN). In a SAN, storage devices such as Digital Linear Tapes (DLTs) and RAID arrays are connected to many kinds of servers via a high speed interconnection, such as Fibre Channel. This high-speed link creates a separate, external network, that's connected to the LAN, but acts as an independent entity. This setup allows for any-to-any communication among all devices on the SAN. It also provides alternative paths from server to storage device. In other words, if a particular server is slow or completely unavailable, another server on the SAN can provide access to the storage device. A SAN also makes it possible to mirror data, making multiple copies available. SANs offer several advantages. First, they allow for the addition of bandwidth without burdening the main LAN. SANs also make it easier to conduct online backups without users feeling the bandwidth pinch. When more storage is needed, additional drives do not need to be connected to a specific server; rather, they can simply be added to the storage network and accessed from any point. Another reason for the interest in SANs is that all the devices can be centrally managed. Instead of managing the network on a per-device basis, storage can be managed as a single entity, making it easier to deal with storage networks that could potentially consist of dozens or even hundreds of servers and devices. You can connect almost any modern server to a SAN, because SAN-support hardware and software spans most PC midrange and mainframe platforms. Ideally, a SAN will lighten your server's workload by offloading many storage-related server tasks to the SAN and by better allocating storage resources to servers. The most important piece of any SAN architecture is the underlying network technology that drives it. You can use ordinary Fast Ethernet, but Fibre Channel is emerging as the technology of choice too for SAN implementations. Fibre Channel was developed by ANSI in the early 1990s as a means to transfer large amounts of data very quickly. Fibre Channel is compatible with SCSI, IP, IEE 802.2, ATM Adaptation Layer for computer data, and Link Encapsulation, and it can be used over copper cabling or fibre-optic cable. 7. Note the advantages of a SAN. 8. Match the terms 1-6 with the statements A-F.
9.Using information from the text, mark the following as True or False. Correct the false ones.
1. In the traditional storage model, it is always possible for every user to access each storage device. 2. Hanging storage devices off servers is the most basic way of expanding storage capacity. 3. The distance limitation of SCSI affects the direct connection of storage devices to a server. 4. A SAN is not usually connected to a LAN. 5. All devices can be centrally managed in a SAN. 6. Fast Ethernet is becoming the most popular type of interconnection for SANs.
WRITING ACTIVITIES.
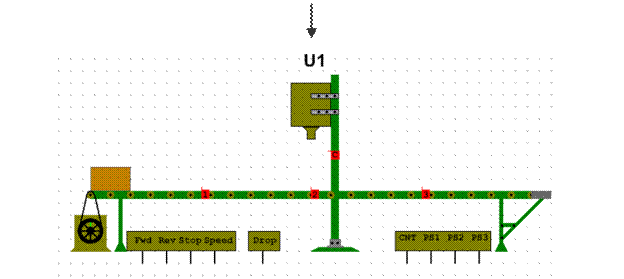
1.Study this diagram of a firewalled network system. Write a description of how it operates. You may need to do some research on firewalls to supplement the diagram. Your description should answer these questions:
Suggested online resources:
http://www.thefreedictionary.com/firewalled http://encyclopedia.farlex.com/firewalled 2. Write a list of tips to prevent computer infections.
UNIT 6. INTERNET
READING ACTIVITIES
1. Read the text and say if these sentences are True or False. Correct the false ones.
1. The Internet and the World Wide Web are synonyms. 2. Computers need to use the same protocol (TCP/IP) to communicate with each other. 3. Web TV can provide access to the Net. 4. ADSL and cable are two types of dial-up connections. 5. External, internal and PC card are types of connections. 6. Information can be sent through telephone lines, satellites and power lines. 7. The computer IP number is a way to identify it on the Internet. FACES OF THE INTERNET
The Internet is an International computer Network made up of thousands of networks linked together. All these computers communicate with one another; they share data, resources, transfer information, etc. To do it they need to use the same language or protocol: TCP / IP (Transmission Control Protocol / Internet Protocol) and every computer is given an address or IP number. This number is a way to identify the computer on the Internet. To use the Internet you basically need a computer, the right connection software and a modem to connect your computer to a telephone line and then access your ISP (Internet Service Provider). The modem (modulator-demodulator) converts the digital signals stored in the computer into analogue signals that can be transmitted over telephone lines. There are two basic types: external with a cable that is plugged into the computer via a USB port, and internal, an expansion card inside the computer. A PC card modem is a different, more versatile option for laptops and mobile phones. At first most computers used a dial-up telephone connection that worked through the standard telephone line. Now a broadband connection, a high data transmission rate Internet connection, has become more popular: either ADSL (Asymmetric Digital Subscriber Line), which allows you to use the same telephone line for voice and fast access to the Internet, or cable, offered by most TV cable providers. The basic equipment has changed drastically in the last few years. You no longer need a computer to use the Internet. Web TV provides email and access to the Web via a normal TV set plus a high-speed modem. More recently, 3Generation mobile phones and PDAs, personal digital assistants, also allow you to go online with wireless connections, without cables. Telephone lines are not essential either. Satellites orbiting the earth enable your computer to send and receive Internet files. Finally, the power-line Internet, still under development, provides access via a power plug.
2. Fill in the word or word combinations from the text.
1. The modem … the digital signals stored in the computer into analogue signals that can be transmitted over telephone lines. 2. A PC card modem is a different, more versatile option for … and …. 3. At first most computers used a … … connection that worked through the standard telephone line. 4. Web TV … email and access to the Web via a normal TV set plus a high-speed modem. 5. The power-line Internet, still under development, provides … via a power plug. 3. Read the text and find the answers to the following questions.
1. What purpose does the Internet address have apart from identifying a node? 2. What data-delivery systems are mentioned in the text? 3. What do IP modules need to know about each other to communicate? 4. How many Internet addresses does a gateway have? 5. What does UDP software do? 6. When does the TCP part of TCP/IP come into operation? 7. What processes are performed by TCP software to provide reliable stream service? 8. What standard protocols are mentioned in the text?
HOW TCP/IP LINKS DISSIMILAR MACHINES At the heart of the Internet Protocol (IP) portion of TCP/IP is a concept called the Internet address. This 32-bit coding system assigns a number to every node on the network. There are 5 various types of addresses designed for networks of different sizes, but you can write every address with a series of numbers that identify the major network and the sub-networks to which a node is attached. Besides identifying a node, the address provides a path that gateways can use to route information from one machine to another. Although data-delivery systems like Ethernet or X.25 bring their packets to any machine electrically attached to the cable, the IP modules must know each other's Internet addresses if they are to communicate. A machine acting as a gateway connecting different TCP/IP networks will have a different Internet address on each network. Internal look-up tables and software based on another standard - called Resolution Protocol - are used to route the data through a gateway between networks. Another piece of software works with the IP-layer programs to move information to the right application on the receiving system. This software follows a standard called the User Datagram Protocol (UDP). You can think of the UDP software as creating a data address in the TCP/IP message that states exactly what application the data block is supposed to contact at the address the IP software has described. The UDP software provides the final routing for the data within the receiving system. The Transmission Control Protocol (TCP) part of as TCP/IP comes into operation once the packet is delivered to the correct Internet address and application port. Software packages that follow the TCP standard run on each machine, establish a connection to each other, and manage the communication exchanges. A data-delivery system like Ethernet doesn't promise to deliver a packet successfully. Neither IP nor UDP knows anything about recovering packets that aren't successfully delivered, but TCP structures and buffers the data flow, looks for responses and takes action to replace missing data blocks. This concept of data management is called reliable stream service. After TCP brings the data packet into a computer, other high-level programs handle it. Some are enshrined in official US government standards, like the Pile Transfer Protocol (FTP) and the Simple Mail Transfer Protocol (SMTP). If you use these standard protocols on different kinds of computers, you will at least have ways of easily transferring files and other kinds of data. Conceptually, software that supports the TCP protocol stands alone. It can work with data received through a serial port, over a packet-switched network, or from a network system like Ethernet. TCP software doesn't need to use IP or UDP, it doesn't even have to know they exist. But in practice TCP is an integral part of the TCP/IP picture, and it is most frequently used with those two protocols. 4. Match the terms 1-6 with the statements A-F.
5. Mark the following statements as True or False. Correct the false ones. 1. Internet addresses are an integral part of the IP protocol. 2. Internet addresses can be written as a series of numbers. 3. UDP software provides the final routing for data within the receiving system. 4. UDP recovers packets that aren't successfully delivered. 5. TCP only works with packet-switched networks. 6. TCP only works when it is combined with IP. 6. What do the following abbreviations mean? IP, UDP, TCP, FTP, SMTP. 7. Read the text and find the answers to the following questions. 1. Name three different email protocols mentioned in the text. 2. Which email protocol is used to transfer messages between server computers? 3. Why is SMTP unsuitable for delivering messages to desktop PCs? 4. Name two host-based mail systems mentioned in the text. 5. Where are email messages stored in an SMTP system? 6. What happens when you use your Web mail account to access a P0P3 mailbox? 7. What are the advantages of using the IMAP4 protocol? EMAIL PROTOCOLS
Although the format of a mail message, as transmitted from one machine to another, is rigidly defined, different mail protocols transfer and store messages in slightly different ways. The mailsystem you're probably used to employs a combination of SMTP and P0P3 to send and receive mail respectively. Others may use IMAP4 to retrieve mail, especially where bandwidth is limited or expensive. SMTP, Simple Mail Transfer Protocol, is used to transfer messages between one mail server and another. It's also used by email programs on PCs to send mail to the server. SMTP is very straightforward, providing only facilities to deliver messages to one or more recipients in batch mode. Once a message has been delivered, it can't be recalled or cancelled. It's also deleted from the sending server once it's been delivered. SMTP uses 'push' operation, meaning that the connection is initiated by the sending server rather than the receiver. This makes it unsuitable for delivering messages to desktop PCs, which aren't guaranteed to be switched on at all times. In host-based mail systems, such as UNIX and Web mail, SMTP is the only protocol the server uses. Received messages are stored locally and retrieved from the local file system by the mail program. In the case of Web mail, the message is then translated into HTML and transmitted to your browser. SMTP is the only protocol for transferring messages between servers. How they're then stored varies from system to system. POP, Post Office Protocol, is a message-retrieval protocol used by many PC mail clients to get messages from a server, typically your ISP's mail server. It only allows you to download all messages in your mailbox at once. It works in 'pull' mode, the receiving PC initiating the connection. PC-based POP3 mail clients can до do this automatically at a preset interval. When you use your Web mail account to access a P0P3 mailbox, the mail server opens a connection to the P0P3 server just as a PC-based application would. The messages are then copied into your Web mailbox and read via a browser. Since P0P3 downloads all the messages in your mailbox, there's an option to leave messages on the server, so that they can be picked up from different machines without losing any. This means that you'll get every message downloaded every time you connect to the server. If you don't clean out your mailbox regularly, this could mean long downloads. When using a Web mail account to retrieve P0P3 mail, be careful about leaving 55 messages on the server - if too many build up, each download will take a long time and fill up your inbox. Many Web mail systems won't recognize messages you've already downloaded, so you'll get duplicates of ones you haven't deleted. IMAP, Internet Mail Access Protocol, is similar in operation to POP, but allows you more choice over what messages you download. Initially, only message headers are retrieved, giving information about the sender and subject. You can then download just those messages you want to read. You can also delete individual messages from the server, and some IMAP4 servers let you organize your mail into folders. This makes download times shorter and there's no danger of losing messages. 8. Discuss advantages and disadvantages of having an option to leave P0P3 messages on the server. 9. Mark the following statements as True or False. Correct the false ones.
1. Different mail systems transfer emails in different ways. 2. IMAP4 requires more bandwidth than the other email protocols. 3. SMTP is used for sending emails from a PC to a server. 4. SMTP delivers messages one at a time. 5. SMTP does not allow a delivered message to be cancelled. 6. SMTP is only one of many protocols used to send mail between servers. 7. POP protocol allows the user to download one message at a time.
10. Match the terms 1-5 with the statements A-E.
WRITING ACTIVITIES
Write an article for a newsgroup of your choice to Computer Communications. The International
|