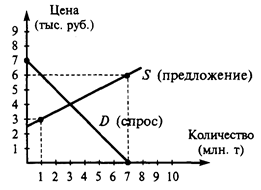
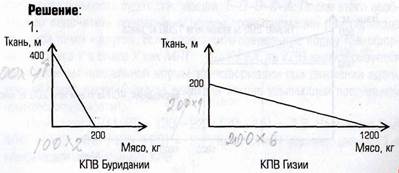
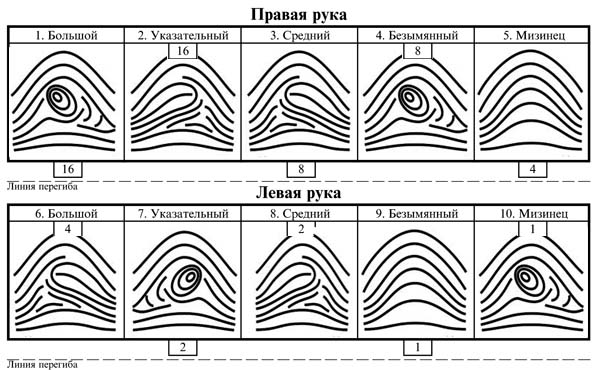
USB Flash Drives Revolutionize Portable Storage but Pose Security Risks for OrganizationsOver the last few years USB Flash Drives have become a must-have item for computer users everywhere. We rely on them to transport all kinds of data including letters, spreadsheets, presentations, music and even movies. The capacity, physical size and speed of these drives has increased rapidly, and with that prices have come down making them an affordable accessory rather than luxury item. They have now completely replaced the humble Floppy Disk as the dominant format for re-writeable, portable storage, and rightfully so - Floppy Disks were well past their sell-by date at the turn of the 21st century. But there are some risks associated with such a small device capable of storing vast amounts of data being kept in the pockets and on the key chains of millions of workers at companies/organizations across the world. Let’s take a look at some of these risks in detail. The first risk is a loss of productivity; workers could use their USB Flash Drives to bring in software that is not suitable for the workplace, such as games or “joke” applications that could cause disruption. Employees could also use the fast internet access usually provided in the corporate network to download illegal or unsavoury material onto their USB Flash Drives that could damage the company’s reputation and potentially cause spyware or adware infections. The second risk is of workers bringing viruses, trojans, malware or adware into the workplace on USB Flash Drives. An example of this would be an employee with poor security on their home computer bringing a file he/she has been working on at home into the workplace on their USB Flash Drive and plugging it into a company machine. This could expose the corporate network to all kinds of viruses or malicious code that may have been transferred on the USB Flash Drive from an unprotected computer. (Alex Culshaw, http://www.articlesphere.com, January, 2009) 4.2. Indicate the paragraph that explains the advantages of USB Flash Drives and their popularity with computer users. Read this paragraph and define its main point. Summarize the paragraph in no more than two sentences. Begin with: The article informs… The article discusses/analyzes …. The article raises up a question of… 4.3. Indicate the paragraphs that describe some of the risks associated with such small devices. Read them again and condense their content into 3 statements using the phrases: The article also considers …. Attention is given to …. The article touches upon ….. Particular emphasis is placed on …. 4.4. Indicate the paragraphs where the solution to the problem of data leakage is suggested. Read these paragraphs and compress their content into statements using the phrases: A solution to the problem of … is proposed. Special emphasis is placed on… The article is of (no) particular interest…. The article is of (no) professional interest, because…. 4.5. Summarize the content of the article.
Text 5 5.1. Look at the title of the article and think what exactly it is going to be about. Check your guesses.
How to Really Trust a Mathematical Proof
|